As the world gets more digitized, the playground for hackers increases every day. In 2017, cyber-attacks were prominent on both businesses and individuals globally.
It is estimated that in December of 2017, about 33.8million records leaked onto the internet. The number was even bigger the previous month with 59 million records being leaked. From these numbers, it’s clear that cyber-attacks are now a reality of life. People and businesses must stay cautious to keep their data and network safe.
2017 was the year of significant cyber-attacks. The likes of WannaCry, Locky and NotPetya dominated news cycles because of the severity of the attack and the losses incurred during the whole process. As we do not know what hackers are planning, it’s crucial for an organization and individuals, in general, to be prepared for the worst-case scenarios. In this regard, being safe and prepared means knowing the most prevalent and likely to happen incidents and being ready for such events. Hackers have evolved their methodologies of attack; hence possible victims must also get pro-active to evade surprises in case of a cyber-attack. In that respect, we’ll look at some of the most likely threat you should always be on the lookout for in 2018.
More Cloud Data Breaches
One of the most valuable and popular products on the darknet is personal information. In 2017, there was an attack on the Equifax credit reporting agency. Because the agency checks for credit, they have all an individual’s information including their birth dates, social security and credit card numbers, among others. When Equifax was breached, the hackers got away with data on more than half of the US population. This goes to show that hackers are not afraid of going for the whales in the ocean. Companies dealing with information will be on their radar in 2018, especially in the case of data brokers who usually have information such as people’s web browsing habits.
Although the giant companies such as Google IBM and Amazon have the muscle to fight off attacks on the cloud, smaller companies do not. As such if their encrypted data was stolen and held for ransom, they would be more likely to pay up.
Crime-As-A-Service (CaaS)
Traditionally, hackers have been known to either work alone or as a group. However, with time they have become smarter. Hackers and malicious criminals on the internet are now collaborating and organizing. Regarding organized crime, gangs are usually a top pick. In 2018, more coordinated hacking attacks are expected.
Botnets, DDoS and IoT
The Internet of Things has been a remarkable thing to watch. IoT has revolutionized the way we think about accident prevention, transportation planning, safety and even the self-driving cars. This impact has also been felt directly into our homes with assistants coming up such as Cortana, Alexa, and Siri; voice control is at an all-time high. However, other home devices have also been given the “smart” feature. This means that machines such as fridges, televisions, baby monitors and toasters are connected to the internet and as such are a gateway for intruders. In 2016, hackers mobilized an army of home devices to shut the internet in some parts of the country. In theory, this method can also be used to cripple services at an organization.
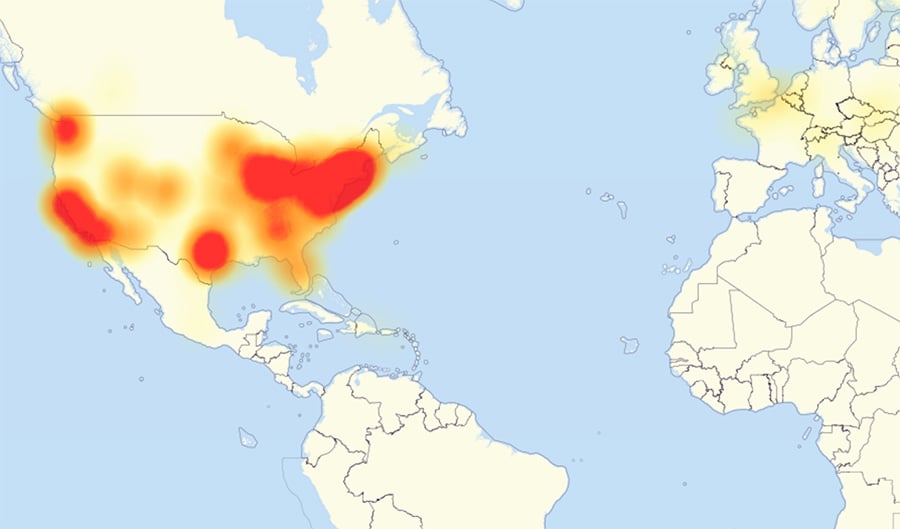
The 2016 Dyn cyberattack
Data-rich institutions will be a huge target for hackers in 2018. Industries such as healthcare and education will more likely receive a bigger hit this year. Even though IoT is making healthcare better, it’s also creating a doorway for others to move through. These are prime targets for malicious users because unlike the tech conglomerates, these institutions lack the necessary power to control and secure system endpoints tightly. As such, with the right amount of aggression or motivation, they can easily bypass security and get to other more sensitive information about patients.
Social engineering, spam and phishing
Since 2015, the leading cause of data breaches is human error. Roger Grimes, an authority at CSO suggested that social engineering and unpatched software were to blame for security breaches nearly 100% of the time. In 2018, social engineering is expected to grow to an all-time high and become more complex.
Spam and phishing will also go up a notch higher. Since these days clients are aware of phishing schemes, they will often perform a google search to confirm whether there was an attack on an institution such as a bank. Because hackers are aware of this, they will most likely also populate some articles on the internet supporting their claim. So, when a person is not careful, they might fall into the trap and end up giving out private, sensitive information.
Cryptojacking
Presently, cryptocurrency has the world in a frenzy. Since Bitcoin broke the $10000 mark, it has been more valuable than gold. As such, hackers are also looking for a way to capitalize on this rush. Since mining cryptocurrency requires a lot of processing power to solve complex mathematical problems, hackers have found a way to mine the currencies in a passive mode.
Hackers are creating malware and leaving it to run in the computer’s background which allows for your machine to mine cryptocurrency even without your knowledge. As a result, computers and cell phones are being infected and mining the currency in the background. Mining cryptocurrency is a resource hungry process; thus, users will note a dip in processing power. Therefore, tasks the computer used to breeze through are not as simple anymore.
Since these hackers want as much processing power on the job as possible, they will also compromise websites and hosting companies with weak security features and mine cryptocurrency.
The cybersecurity scene will be quite eventful this year. While hackers are getting smarter, organizations and people at large must also change accordingly. Evolving with the security advancements ensures prevention of attacks. Improvements in cybersecurity such as using artificial intelligence to enforce security is a huge leap forward and could mean big things for the whole industry.