Article originally posted on ProgrammableWeb
A new self-serve risk assessment tool is now available in private beta for API providers who want to test the security robustness around their API architecture and design.
Sapience offers an online tool that lets providers check the security risk of their APIs across 12 risk vectors, including SQL and CRLF injection, buffer overflows, cross site scripting and more.
API security is becoming recognized as a specialist area with its own risk vectors. As APIs become a more common business tool for enterprise and startups, savvy hackers are utilizing methods particularly aimed at targeting the vulnerabilities that may come with poorly designed or managed APIs. Like scraping bots, API-specific security threats may aim to download excessive data, cause denial of service attacks, or introduce errant code that creates chaotic API querying.
Sapience is a stand-alone security testing product from apiware, a consultancy service specializing in API first design and review. Thomas Cornelius, co-founder of apiware and Sapience says the idea for the product came from apiware’s consultancy work where many clients had the same security challenges. Cornelius’ team wanted to create a product that could help their clients regularly check and manage the security threats to their APIs: “We wanted to allow users to scan their APIs on a daily basis and to identify solutions to resolve those vulnerabilities,” says Cornelius.
The Sapience Process
Cofounder Alexander Menzheres describes the Sapience process:
We support RESTful APIs and you can get started by importing an API definition format file, create an API profile manually, or enter an API definition URL.
Menzheres says Sapience leverages the API Transformer technology to be able to read API Blueprint, Swagger, RAML and other definition formats.
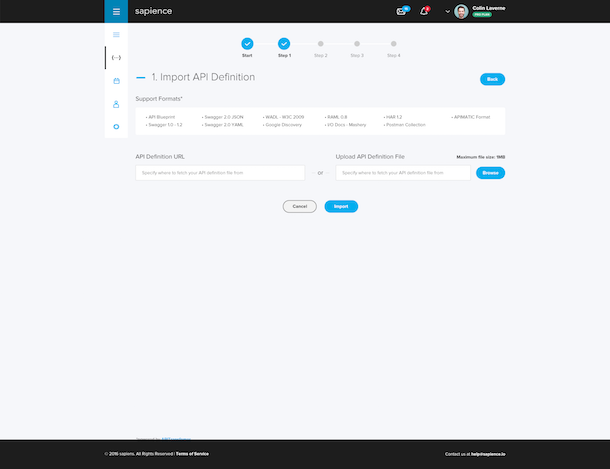
Menzheres and Cornelius say their approach has been designed for API providers rather than for consumers who want to check the vulnerabilities of the APIs they are using. So in order to conduct the security assessment, the API provider must provide confirmation of ownership, such as a DNS record or upload an API file before Sapience shares their assessment.
Sapience then lists all the resources within an API (which is also useful for non-engineers, says Menzheres) and tests each endpoint individually. “The idea is that we then try to reach all endpoints, sending different threats and vulnerability tests and we show you the progress. The time of the scanning depends on the number of endpoints in an API.”
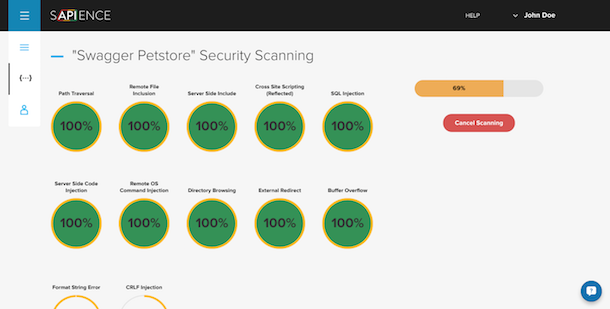
A Template-Driven Product Approach
Once the scan is completed, Sapience provides a dashboard overview of the results, identifying areas where API architecture could be strengthened to reduce security threats. A list of suggested remediation actions is given based on the results uncovered. In this way, Sapience can offer a self-serve product that identifies risks and provides some guidance on how to bolster security in a scalable, product-centric way.
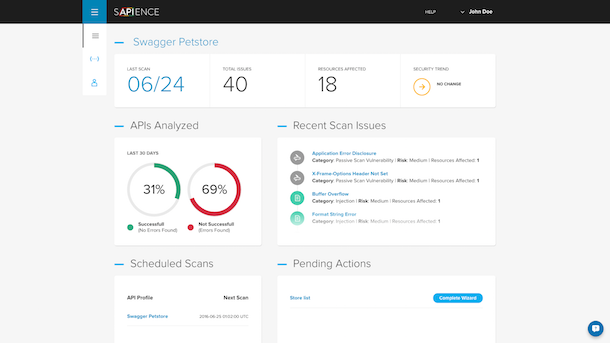
Cornelius says this template-driven product design is ideal for the initial product, and hopes to be able to extend into specific verticals, and build more tools when the service begins to identify the most common threat risks. “As we get a better understanding of the aggregate security issues facing APIs, we are going to build out our vulnerability of tests in the backend that will suit vertical industries. At the moment, we have a set of vulnerability tests, and as we grow, we learn more about these vulnerabilities,” he says.
So far, the most frequent threats that the service is finding for API providers is API error disclosure: “When something happens and your app crashes, it just shows you data and so a hacker can get information from this log,” Cornelius warns.
Embedding Security Checks into Continuous Integration Processes
Like most DevOps, SecOps and lifecycle tools now entering the market, it is essential that they offer some connection with continuous integration (CI) tooling. Cloud-based technologies operate in a global, 24/7 usage environment and continuous integration and continuos delivery enable app and infrastructure updates to be deployed without taking whole systems offline for long periods of time. Sapience integrates with CI tools. Menzheres explains:
We support triggering scans by webhooks and integrating with CI. Every time you update a new commit, you immediately run a scan so that everything is tested for vulnerabilities and integrated with New Relic, Jenkins or any CI. We also plan to add integrations with Jira and GitHub.
Security Certification
Cornelius says that interest in addressing API security within business sometimes comes from a genuine interest in ensuring APIs are built to the highest standards, using industry best practices. But pragmatically, Cornelius also admits that sometimes interest in security comes from the need to check off to higher ups that ‘security has been dealt with’:
Sometimes, it is the mid-manager who says we need some security answers and some certification. Another main driver comes from startups that want to make sure that everything is secure. They are running at a hundred miles an hour and want to make sure nothing is slipping through the cracks. Some engineers want the best for their platforms and want their clients to be secure. And sometimes, in enterprise, they need some seal of approval to show the world they care about security.
“We were surprised at who has shown interest in our beta already,” says Cornelius. “We have new tech giants with established platforms, enterprise clients where the API manager wants to do security right, and business managers who need to cover their ass that they have actually done some security testing. But the bulk are really solid engineers who just want to get the security issue right.”
Cornelius says that Sapience provides a certification system so that API providers can demonstrate that their API meets current robust tests against common API security threats. After API providers run a scan and resolve the identified security concerns, they can add a security seal to their website to demonstrate their robustness. As future scans are conducted, customers have 48 hours to fix the vulnerabilities identified, and if not resolved, the display of the API security certification is disabled. “This allows them to showcase to their dev community that they do take security seriously,” says Cornelius.
API providers interested in testing their API for security vulnerabilities can sign up for the private beta now at sapience.io.